
What are ZKPs
In simple terms, Zero Knowledge Proofs enable one party (prover) to cryptographically prove the possession or validity of a piece of secret information (witness) to a second party (verifier), without revealing that information.
This cryptography primitive was first introduced by Shafi Goldwasser, Silvio Micali, and Charles Rackoff in 1985, in their research work titled The Knowledge Complexity of Interactive Proof-System which helped lay a solid foundation for the growth of zero-knowledge proofs.
Cryptography has always been a key tool in enabling private communication on the blockchain using encryption and digital signatures. With the invention of ZKP, this breakthrough expanded the use of cryptography for private and honest computations, increasing privacy, security, and scalability on blockchain platforms.
The following are the characteristics of a zero-knowledge protocol:
- Completeness: If the statement is true, the verifier can confirm or be convinced of the honest fact by the prover.
- Soundness: If the statement is false, the prover can’t convince the verifier to believe it is true.
- Zero-Knowledge: The verifier knows nothing more other than the validity of the statement.
How does ZKP work?
The ZKP proving process starts with the prover randomly choosing a question from a set where only one with knowledge of the secret information (witness) is able to answer, computing the answer, and sending it to the verifier.
To ensure that the prover did not get lucky with a wild guess, the verifier needs to put up a series of tests/queries (challenge) to be convinced of the prover’s claim. Each time this happens, the prover needs to be able to compute and give the verifier the correct answer (response).
The above illustrates interactive ZKP, which requires multiple back-and-forth interaction between provers and verifiers. ZKP can also be non-interactive: where only one round of communication is needed between participants (prover and verifier). First proposed by Manuel Blum, Paul Feldman, and Silvio Micali, non-interactive ZKP makes use of a shared key between the prover and verifier to compute the zero-knowledge proof, making it significantly more efficient than interactive ZKP.
Why do we need ZKP?
ZKP gives users a way to prove ownership or possession of sensitive information—such as passwords, credentials, or identification—without revealing them, enabling far greater privacy and data security than possible with traditional systems.
ZKP Use Cases
The advent of ZKP was accompanied by tremendous interest by developers and researchers, and rapid growth in its application in systems where security and privacy are important, including the blockchain industry. The following are some of the use cases of zero-knowledge proofs in the blockchain industry:
- Private Transactions / Anonymous Payments
By default, blockchains are designed to be public and transparent, with every transaction visible on-chain. This enables anyone to track the on-chain activities of any user, which creates a privacy issue for users. By integrating zero-knowledge technology, transaction data like sender/receiver addresses, asset type, quantity, and other transaction details can be shielded, thus providing individual users with privacy and security while keeping the blockchain public. Some real world implementations of this use case include Tornado Cash, Monero, Zcash.
- Decentralized Identity and Authentication
Unlike existing identity management systems that require users to reveal personal data to be validated, ZKP-based systems allow users to verify their identities without divulging them, thus enhancing security. ZK-DID positions itself as a secure and verifiable credential and identity system
- Verifiable Computation
With ZKP, transaction execution can be moved off-chain, by having the computing entity submit a ZK proof to prove the correctness of execution along with the results to be applied on-chain. This greatly increases the scalability of a chain by minimizing computational load on the primary blockchain. A prominent real-world example of this use case is Zero-knowledge rollups (ZK-rollups).
- Blockchain-based Messaging
It is perceived that the current messaging system encrypts messages but only ‘in transit’, and are thus accessible by the service provider. This access to data enables service providers to build search functionalities and other features, or to scan for illegal and unacceptable content. This could lead to data being read and misused by anyone who has access to the stored messages on the third-party system. This is a major concern where privacy is very important. With ZKPs, users can be sure of end-to-end trust without having to worry about leaking information to the client program or service providers.
- Online Voting
ZKPs can allow voters to vote online anonymously and with proof to verify that their vote was included in the final vote count. A real world example of this use case is zkVoting.
Types of Zero-Knowledge Proofs
The following are the prominent non-interactive Zero Knowledge Proofs:
ZK-SNARKs
ZK-SNARKs, an acronym for Zero-Knowledge Succinct Non-Interactive Argument of Knowledge, was first introduced in a paper by Eli Ben-Sasson, Alessandro Chiesa, Daniel Genkin, Eran Tromer, and Madars Virza in 2014.
How it works
ZK-SNARKs work based on the following:
a. Set-up: A set-up to construct and determine the initial state of the prover and verifier. It uses a combination of public and private keys or a common reference string.
b. Proving key: A private key that is used to generate a proof.
c. Verifying key: A corresponding public key which is in turn used to verify the proof.
The ZK-SNARK protocol has the following qualities:
- Zero-Knowledge(ZK): means that the verifier has no information other than the validity claim given by the prover.
- Succinct: simply means that the proof size is small thus making verification easy and quick.
- Non-interactive: little or no interaction is required between the prover and the verifier.
- Argument of Knowledge: in simple terms refers to a malicious actor not being able to cheat the system without providing the knowledge to support their claim.
ZK-STARKs
ZK-STARKs stands for Zero-Knowledge Scalable Transparent ARgument of Knowledge, a type of non-interactive ZKP whose first papers were published in 2018 by Eli Ben-Sasson, Iddo Bentov, Yinon Horeshy, and Michael Riabzev.
The ZK-STARK protocol has the following features:
- Zero-knowledge(ZK): means that the verifier has no information other than the validity claim given by the prover.
- Scalable: With this tech, computing transaction execution and storing data can be done off-chain, with a single STARK proof to verify their validity on-chain. Scalability of blockchain infrastructure is therefore made possible by its capacity to batch thousands of transactions for on-chain verification at a cheap gas cost.
- Transparent: uses publicly-available randomness to generate parameters, eliminating the need for a trusted setup.
- Argument of Knowledge: implies the same meaning as one stated above.
Bulletproofs
The bulletproof protocol is a type of non-interactive zero-knowledge proof developed by Benedikt Bunz, Jonathan Bootle, Dan Boneh, Andrew Poelstra, and others in 2017. It makes use of some of the logic behind SNARKs and confidential transaction to improve proof performance both in terms of proof size and verification time.
Here’s how bulletproof works under the hood:
- Bulletproof makes use of the Pedersen Commitments to ensure that values are validated without divulging them to the public.
- In order to generate short tests ZK, and a non-interactive feature, Bulletproof leverages the Fiat-Shamir heuristics, a cryptographic signature system that enables the protocol to verify proof quickly without a trusted setup.
- On the other hand, the bulletproof protocol is based on the assumption of a discrete logarithm. For a deep dive into the workings of Bulletproof, refer to this guide.
Comparing the different ZKPs
Here’s a quick comparison of the three zero-knowledge protocols detailed above:
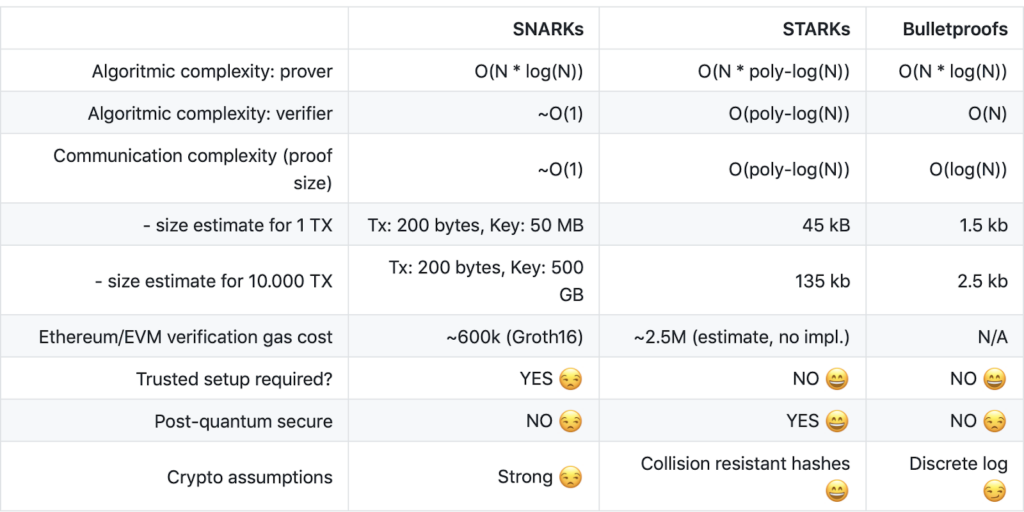
Zero-Knowledge Proof on Klaytn
As Klaytn is Ethereum equivalent, the majority of ZKP tools and libraries created for Ethereum are compatible with Klaytn.
Therefore, the integration of ZKP on Klaytn will provide developers and researchers with a variety of chances to create various use cases and applications where ZKPs might be useful.
Prominent industry implementations of ZKP
- Zcash is one of the prominent privacy-preserving protocols that use ZK-SNARKs. With the use of ZKP, transaction data such as sender/recipient address, and value are shielded, and blockchain networks allow nodes to validate transactions without needing to access transaction data.
- StarkWare: A ZK tech for scaling Ethereum. This protocol invented ZK-STARKs, to enforce the integrity and privacy of computations on blockchains, using novel cryptographic proofs and modern algebra.
- zkSync: zkSync Era is the layer 2 protocol that scales Ethereum’s security and values through zero-knowledge cryptography.
- Monero: Monero, a decentralized cryptocurrency, leverages privacy-enhancing technology to hide transactions to achieve anonymity and fungibility. Monero has been a pioneer in the implementation of the bulletproof protocol within its blockchain.
- Panther protocol is a decentralized protocol that enables interoperable privacy in DeFi using zero-knowledge proofs. With ZKP baked into Panther protocol, users can own zAssets which can be used to execute private and trusted defi transactions across multiple blockchains.
- zkVoting: zkVoting is the world’s first high-level blockchain-based online voting app that guarantees secret voting and verification.’
- ZK-DID: ZK-DID is a verifiable credential system that is secure, interoperable, scalable, and easy-to-use. It ensures users privacy is guaranteed with the use of advanced zero-knowledge proof technologies.
Challenges of ZKPs
- Computation Intensity: Executing a ZKP requires both a proving algorithm and a verifying algorithm, making it computationally intensive. This makes ZKPs unsuitable for slow or mobile devices. In particular, proving computation cost increases when cryptography (not ZK friendly) is applied to circuit computation.
- Design ZkEVM Challenge: zkEVM that is 100% compatible with native EVM is difficult to build.
- Security: In order to satisfy the three properties of ZKP (Completeness, Soundness, and Zero-knowledge), it is necessary to check that there are no security vulnerabilities in circuit configuration, library use, development, tools, and technologies.
Conclusion
In this article, we covered the introductory basics of zero-knowledge proofs and their use on the blockchain. To further explore building using the ZKP protocol, please refer to the following resources:
